This article is a step-by-step guide to configure single sign-on (SSO) Authentication using the Security Assertion Markup Language (SAML) authentication mechanism. SAML is an XML-based authentication mechanism that provides SSO capability between different organizations by allowing the user authentication without sharing the local identity database. As part of the SAML SSO process, the new Parallels® Remote Application Server (RAS) Enrollment Server communicates with Microsoft Certificate Authority (CA) to request, enroll and manage digital certificates on behalf of the user to complete authentication without requiring the users to put in their Active Directory (AD) credentials.
Service providers and enterprises with multiple subsidiaries (acquisitions) don’t have to maintain their own internal identity management solutions or complex domains or forest trusts. Integrating with a third-party identity providers (IdP) allows customers' and partners' end users to have a true SSO experience.
As an example, we will review the process of configuring Azure as identity provider.
Prerequisites
To configure SAML in Parallels RAS, you need the following:
1. Microsoft Active Directory with the following two user accounts present:
- Enrollment agent user: used to enroll certificates through RAS Enrollment Server (ES) on behalf of the authenticated user.
- NLA User: used to initiate the NLA connection with RD Session Hosts and/or VDI guests.
2. Microsoft Certification Authority in Enterprise mode (more details at Microsoft TechNet):
- Enrollment Agent Certificate Template
- Smartcard Logon Certificate Template
3. Third-party Identity Provider (IdP) such as Azure, Okta, Ping Identity, Gemalto SafeNet, and others. This is where the user accounts will reside. User accounts in IdP must be synchronized with the Microsoft Active Directory environment. Please consult with the provider on how to properly synchronize users.
4. Domain Controllers must have Domain Controller certificates. The certificates on the Domain Controllers must support smart card authentication. Certificates are created using the Microsoft CA certificate template named Domain Controller Authentication. Manually created Domain Controller certificates might not work. If you get an error "Request Not Supported", you may need to recreate Domain Controller certificates. Make sure RD Session Hosts and VDIs have the root certificate issued by the CA in the Trusted Root Certification Authorities store.
5. A Parallels RAS Farm with RD Session Host and/or VDI workloads (running on 64-bit OS).
6. For security reasons, the RAS Enrollment Server is recommended to be installed on a dedicated host. The host should be a standalone server that does not have any other components and roles installed.
7. Both SAML and RAS Enrollment Server configurations are Site-specific settings within the RAS environment. RAS administrators must have "Allow viewing of site information" and "Allow site changes" permissions delegated.
Setting up the Windows Server side to comply with Parallels RAS SAML pre-requisites
Per the prerequisites above, configure Microsoft Certification Authority and certificate templates and add required user accounts. Detailed instructions are available in KB 124813.
Adding Parallels RAS Enrollment Server Agent
Install the Parallels RAS Enrollment Server Agent either manually or from the Parallels RAS Console.
- In Parallels RAS Console > Enrollment Servers > click “+” icon to add a new agent
- In the case of a manual ES setup (RASInstaller.msi > Custom), it is necessary to move the ES host registration key to the following folder: %installation_path%\Parallels\ApplicationServer\x64.
- To export the registration key, open the Parallels RAS Console > ES > Tasks > Export registration key > registration.crt (remote pushing does this automatically)
In the Paralells RAS Console > Enrollment Servers > AD Integration tab, specify the CA and user accounts for Enrollment agent and NLA user you configured and apply the changes.
Final checks
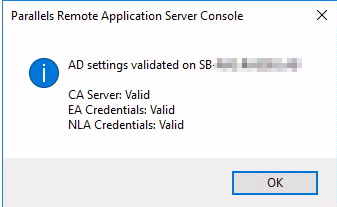
Make sure the Enrollment Agent server status is OK.
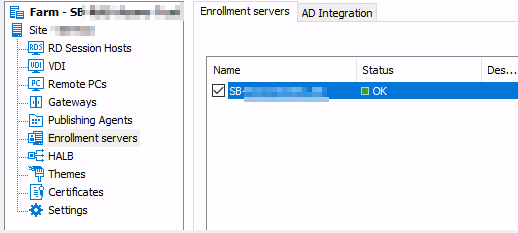
Switch to AD Integration tab and click on Validate AD Integration settings. Make sure that all checks are passed.
Configuration steps
1. On the Azure portal, find Enterprise applications and click New application.

2. Click Create your own application.

3. Enter the name of the application, select Integrate any other application you don’t find in the gallery and click Create.

4. Select Single sign-on from Manage and click on the SAML button.
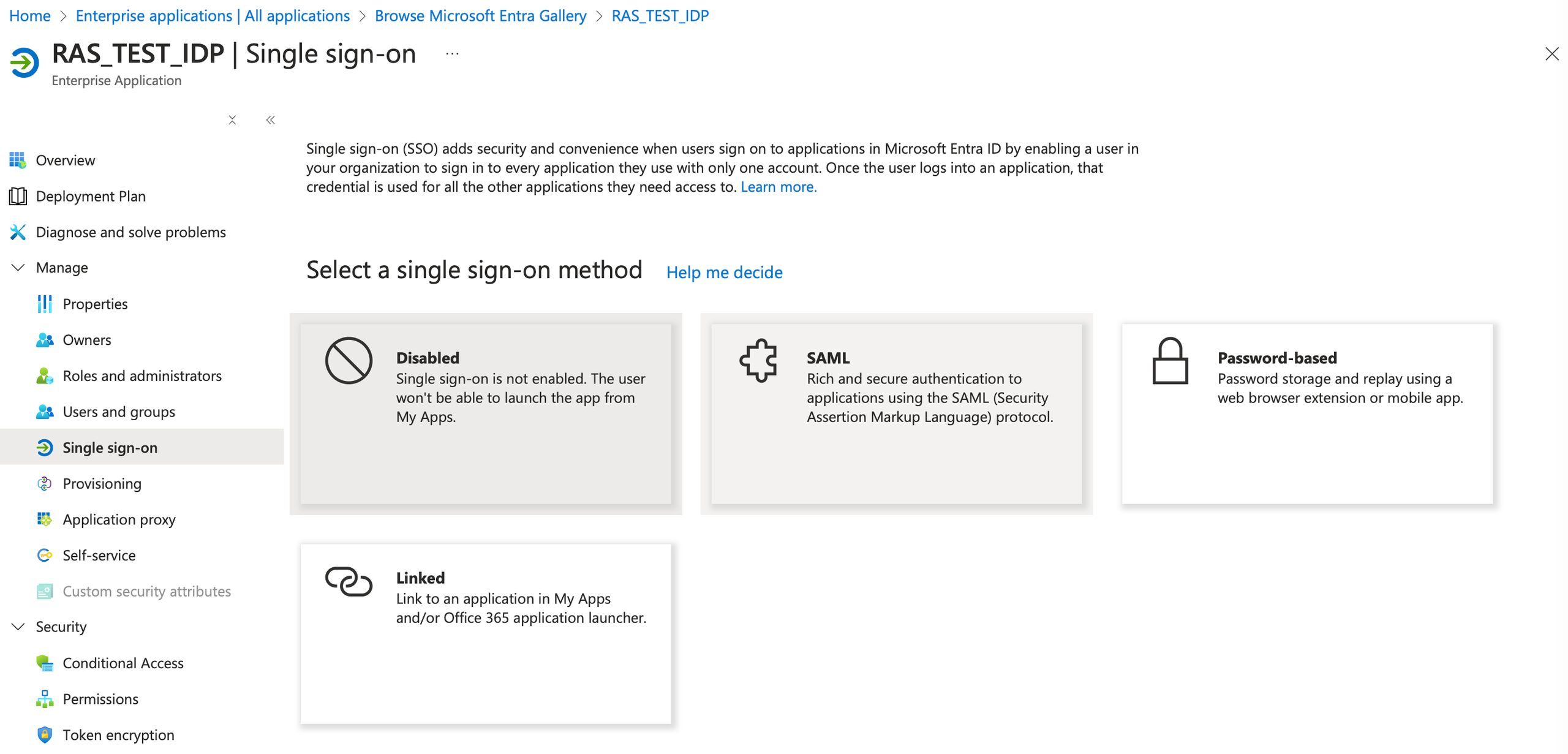
5. Scroll to section 3. Copy the App Federation MetaData Url.
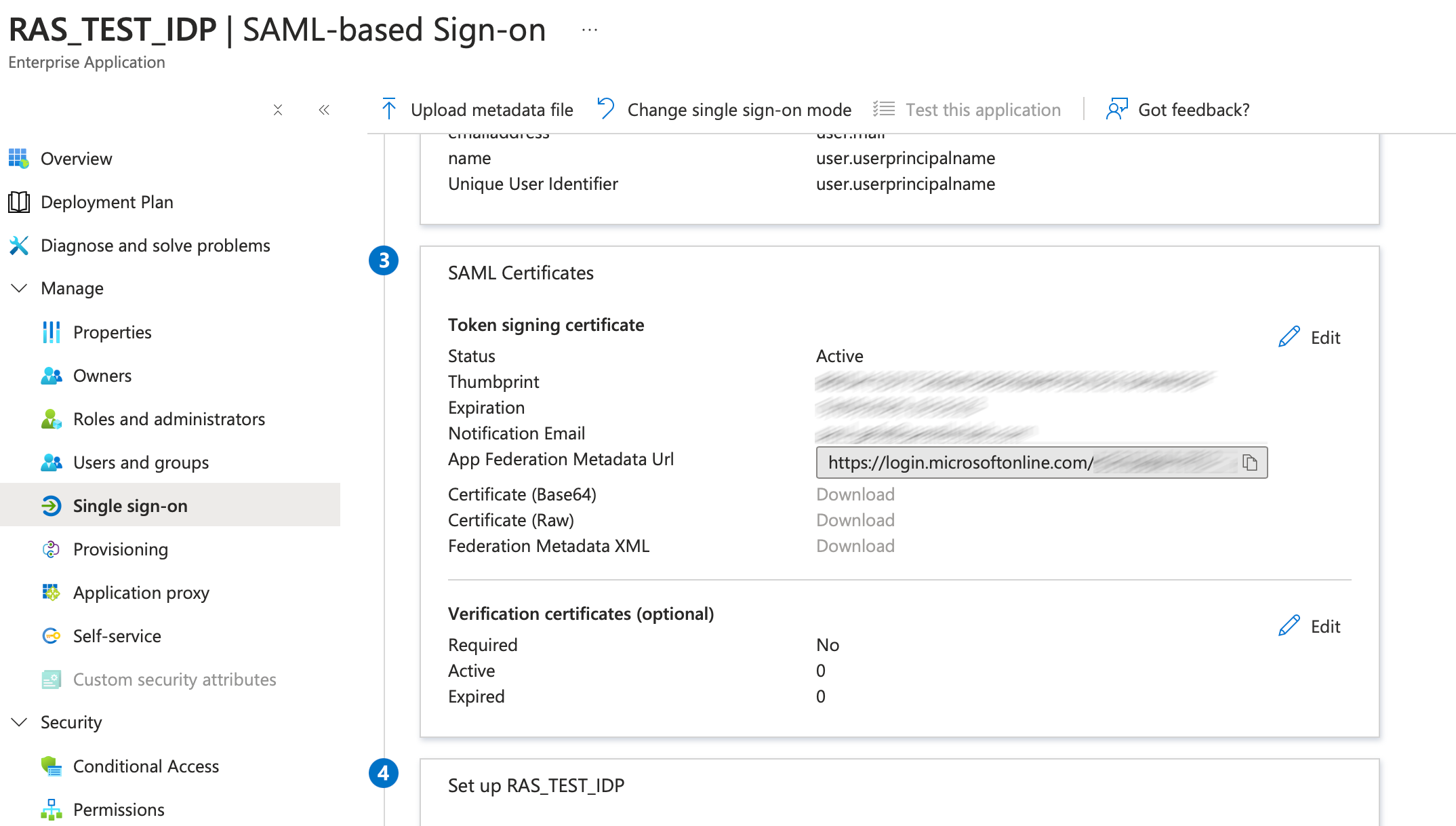
6. Open RAS Console and navigate to Connection category. Switch to the SAML tab and select Add from the Tasks menu. Enter the name and paste the URL in the Import published Idp metadata field. Click Next, then Finish.
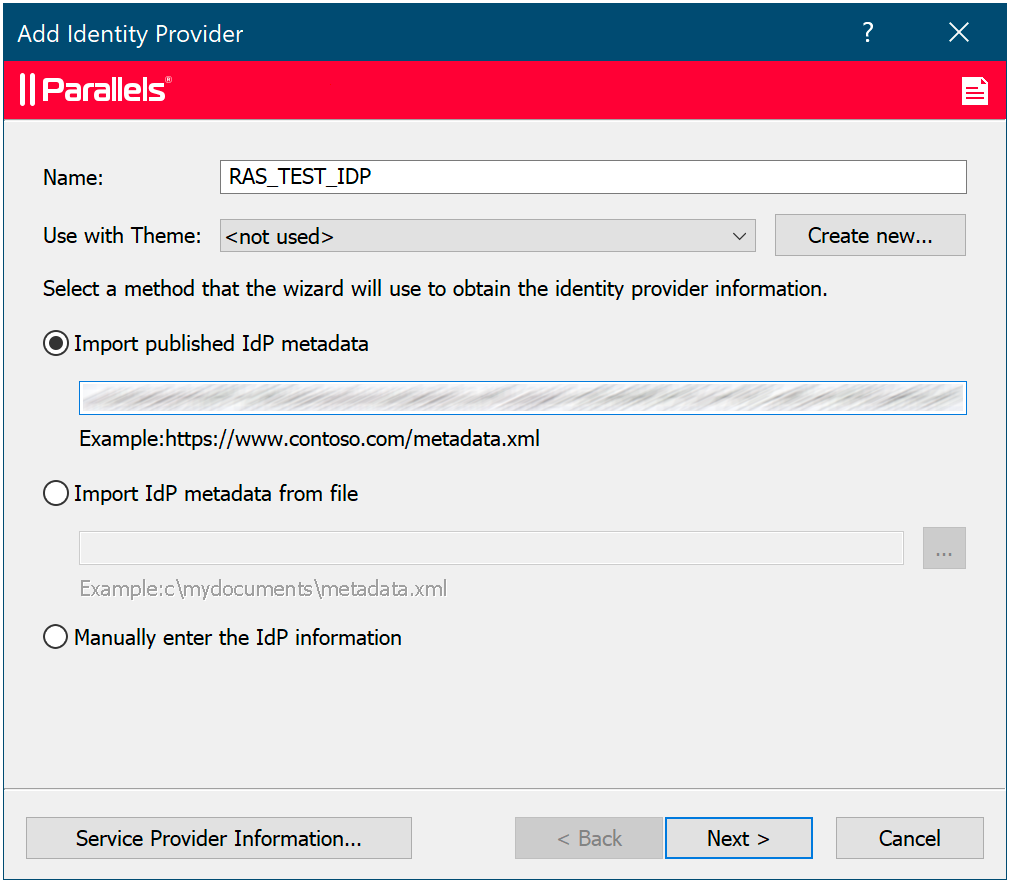
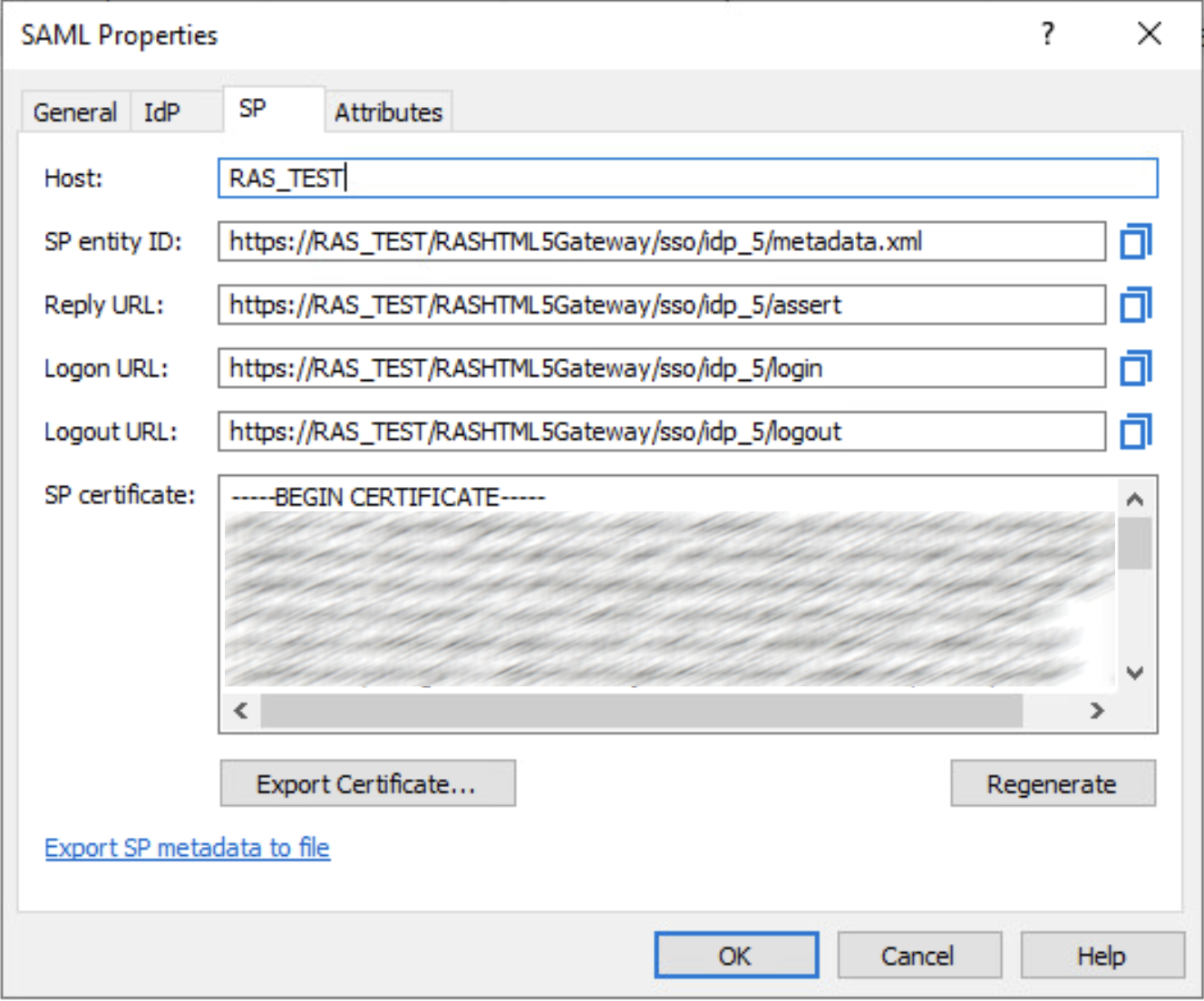
7. Open the properties of the newly created object by double-clicking on it and selecting the SP tab.
8. On Azure portal, scroll up to section 1 and click Edit.
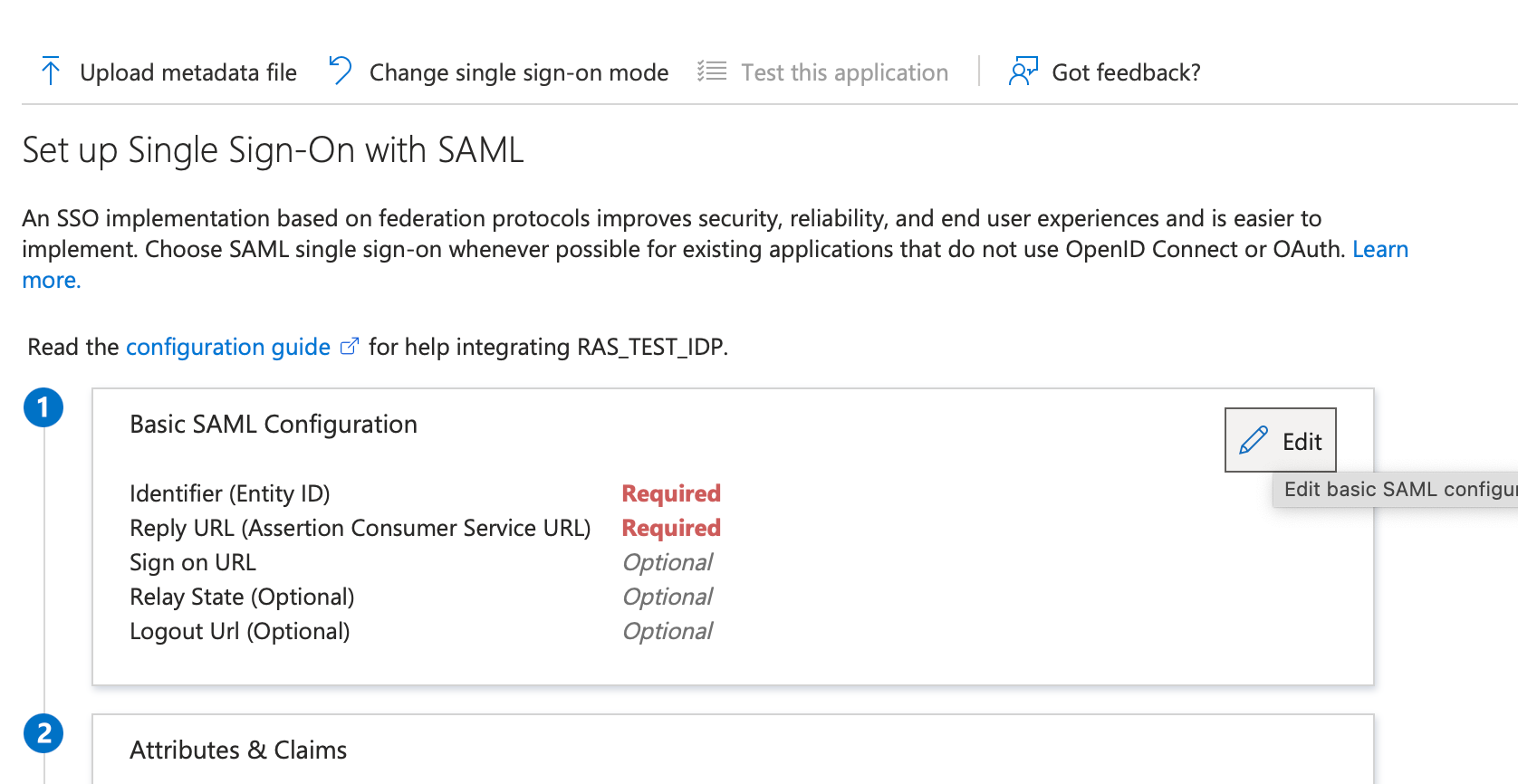
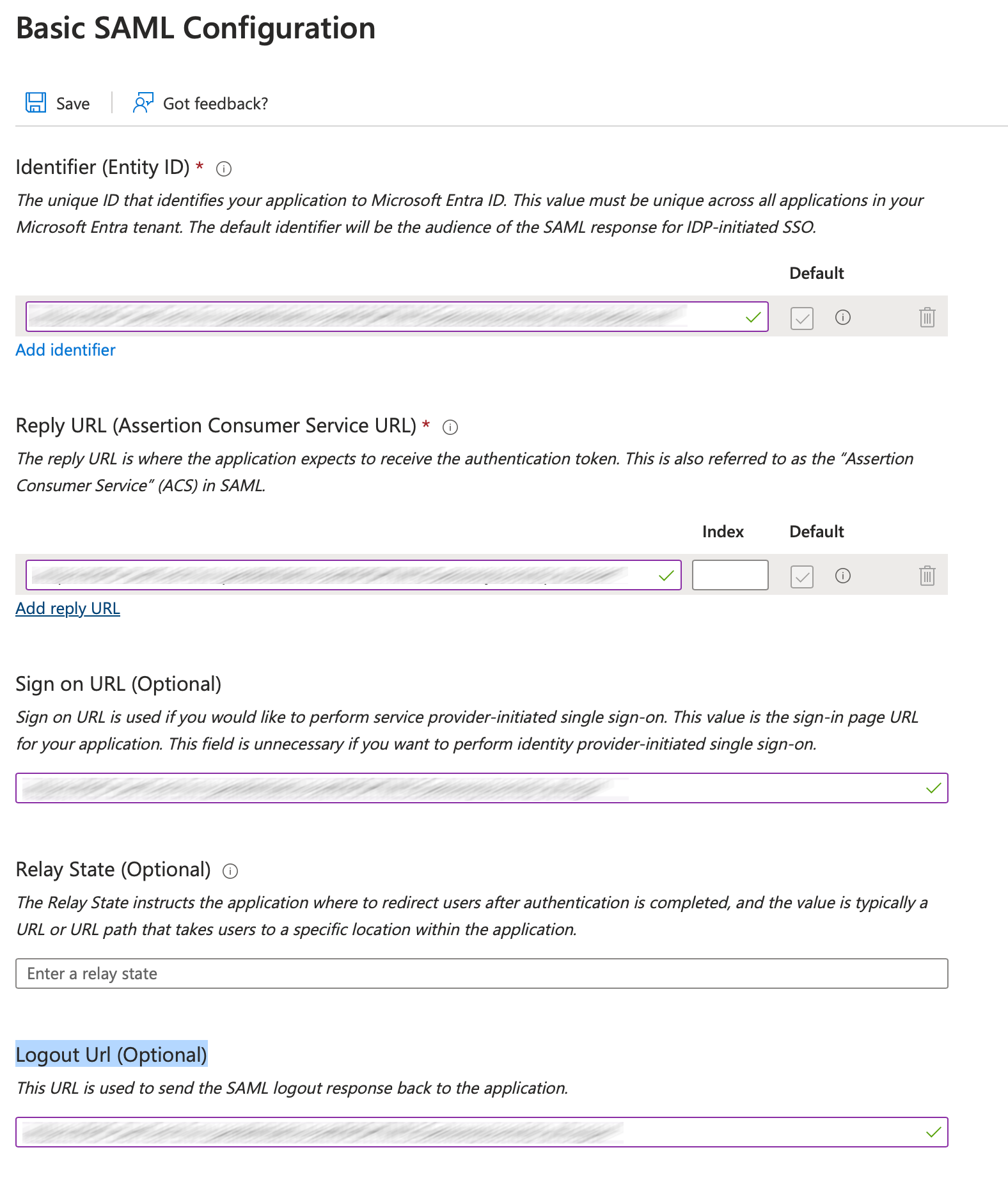
9. Copy the following from the RAS properties window to the Basic SAML Configuration section:
-
SP entity ID → Identifier (Entity ID)
-
Reply URL → Reply URL (Assertion Consumer Service URL)
-
Logon URL → Sign on URL (Optional)
-
Logout URL → Logout Url (Optional)
10. Click on Save under Basic SAML Configuration.
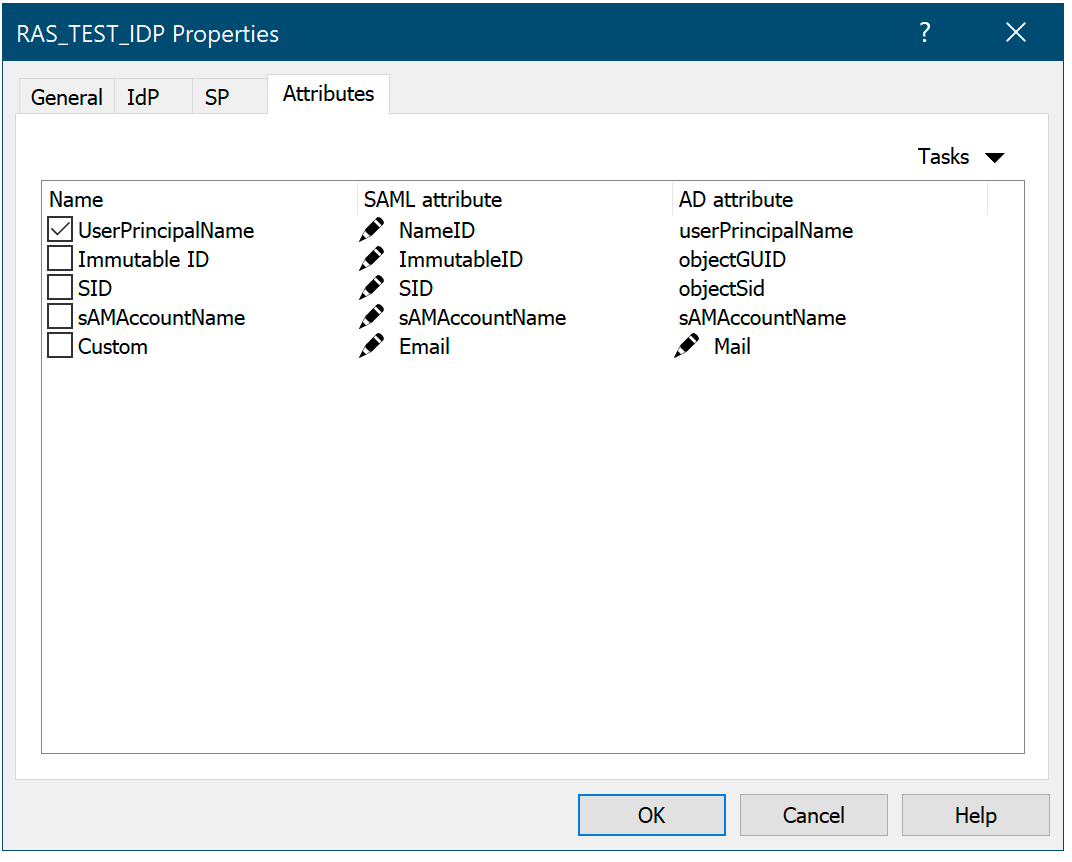
11. In RAS Console, in the IDP properties window, select the Attributes tab.
12. On Azure portal, scroll to section 2 Attributes & Claims and click Edit.
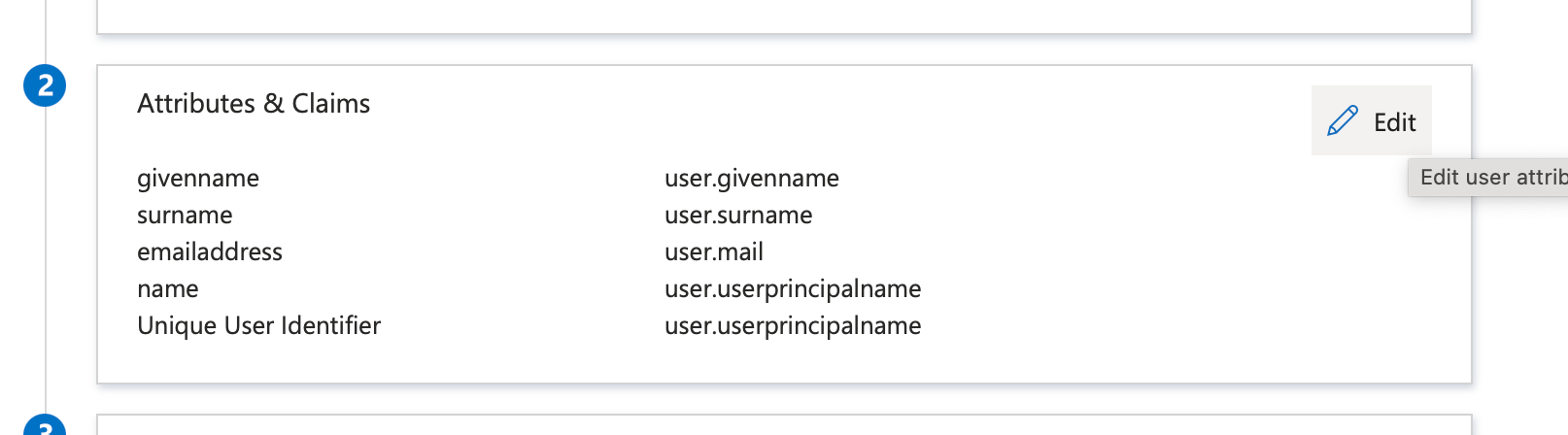
13. This will show what will be available in the SAML claim.

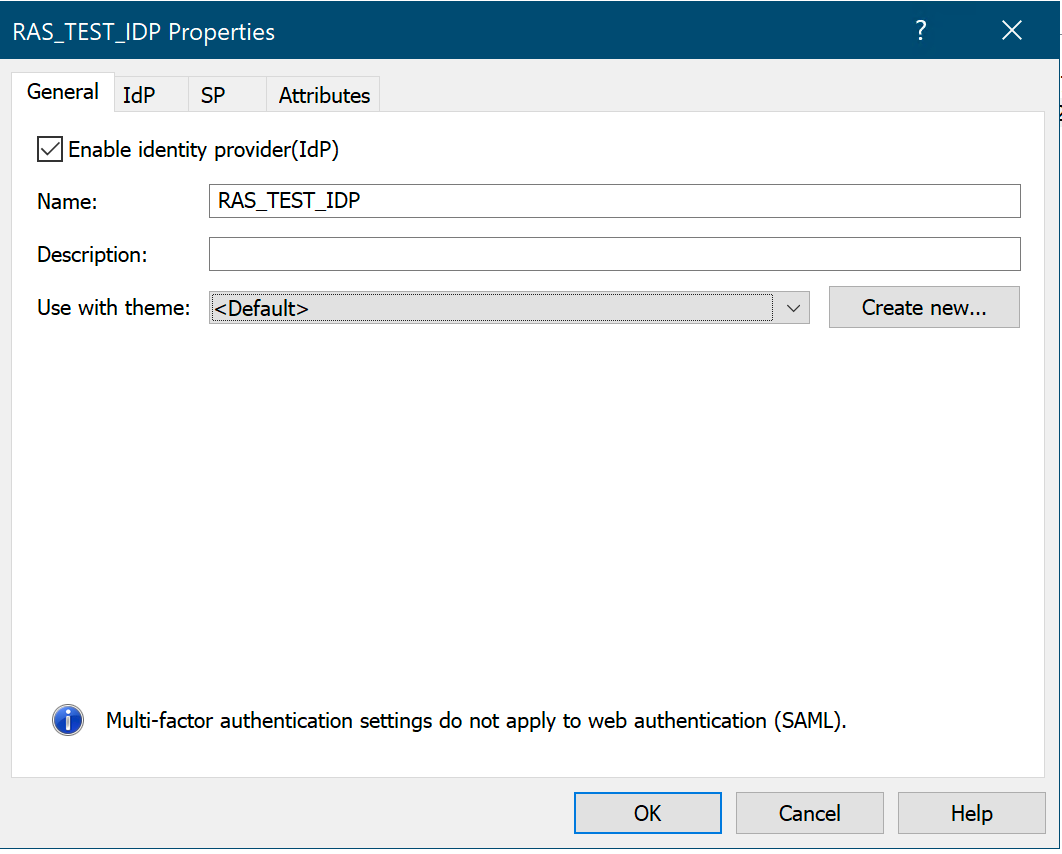
14. Assign the IDP to the theme the users are going to sign in to.:
15. Ensure that Web is enabled as the authentication type.
16. Add the users or groups that will be able to authenticate using the SAML authentication.

Testing connectivity
1. Open the Parallels RAS client.
2. If everything is correct, you will be immediately redirected to login.microsoft.online. Proceed with sign in.


Was this article helpful?
Tell us how we can improve it.