Symptoms
- A published app is failing to start from Parallels Client with the error:
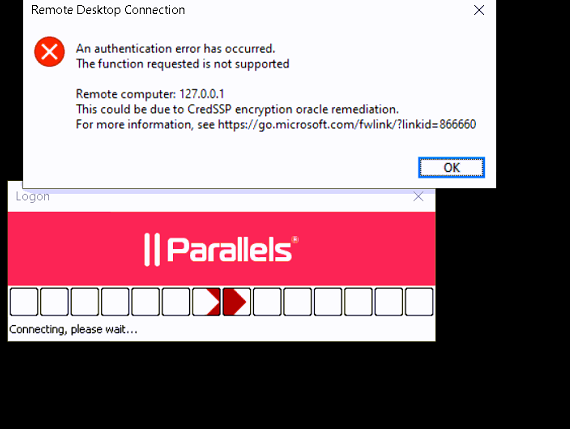
- No issues while launching published applications in the HTML5 Gateway.
- Both, client PC and RDSH have the CVE-2018-0886 CredSSP vulnerability patch installed
Cause
- Outgoing NTLM traffic is prohibited from the client PC by GPO "Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers"
- Inbound NTLM traffic is blocked on the target server by GPO "Network security: Restrict NTLM: Incoming NTLM traffic"
Resolution
Client-side
On the client PC, set the following GPO:
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options > Network security: Restrict NTLM: Outgoing NTLM traffic to remote servers > set to Audit All
Note: Alternatively, you may configure Network security: Restrict NTLM: Add remote server exceptions for NTLM authentication policy setting to specify a list of remote servers to which client devices are allowed to use NTLM authentication while denying others.
Reference:
Server-side
Set the following GPO:
Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options > "Network security: Restrict NTLM: Incoming NTLM traffic" > set to Allow all
Note: Alternatively, you may create an exception list of servers to exclude from this policy setting Network security: Restrict NTLM: Add server exceptions in this domain.
Reference:
Was this article helpful?
Tell us how we can improve it.