Description
In Parallels Remote Application Server v19 static filtering has been changed to expression-based rules:
• Rule can have 1 expression only.
• Multiple rules can be created.
• A rule applies depending on priority - from top to bottom.
• “Deny” has a higher priority than “Allow” and should be placed on the top (above “Allow”).
• Matching method is based on conditions “is” or “is not”.
Expressions format is Permission | Method | Criteria Type | Value
• Permission: “Allow” (match is found, and the published item is shown in the app list) or “Deny” (match is found, but the published item is NOT shown in the app list = explicit access prohibition).
• Method: “is one of the following” or “is not one of the following”.
• Criteria type:
- Users, Groups, or computer SIDs (in policies only),
- Gateways.
- Themes.
- Client device names.
- Client device OS, IP addresses.
- MAC address.
- Value: object.
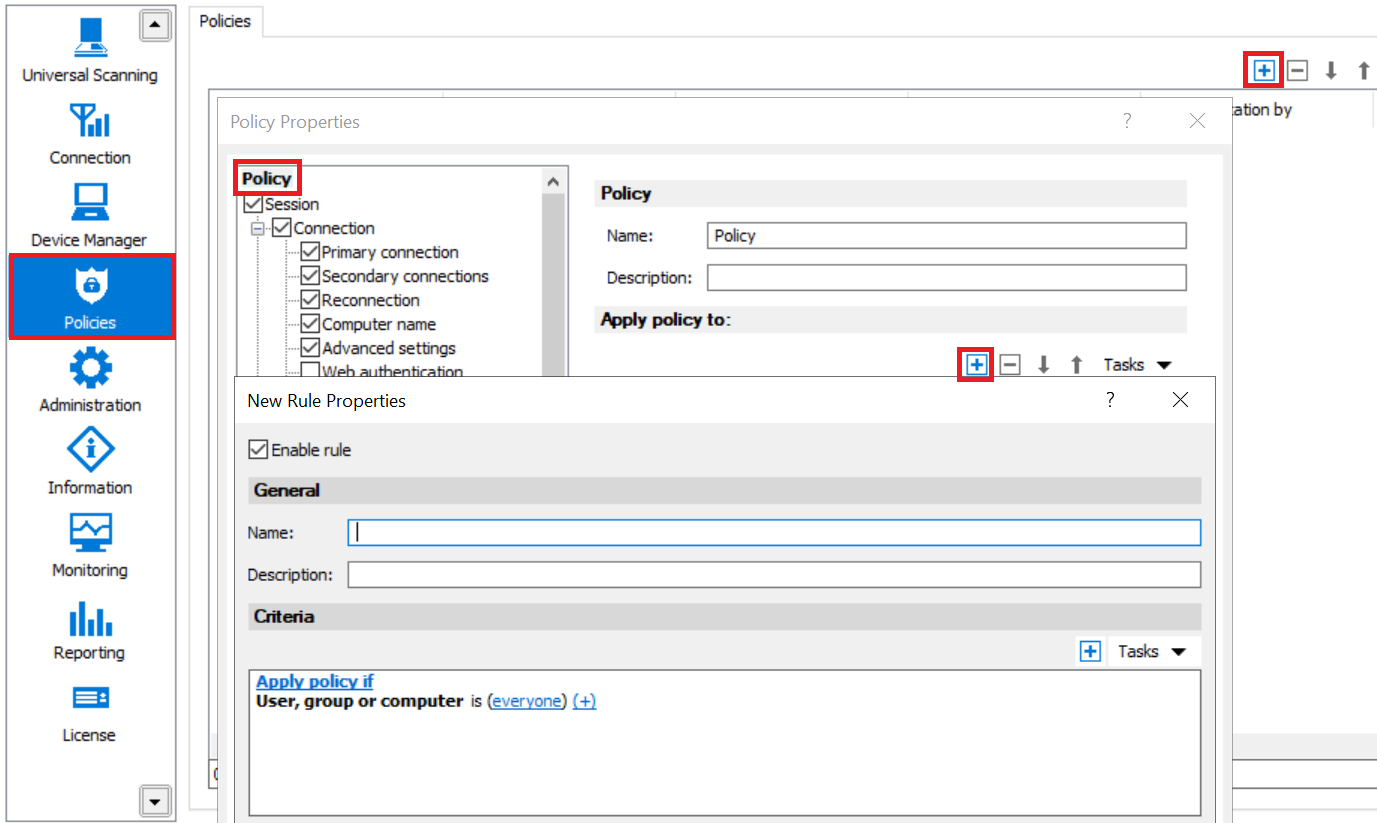
Using expression-based filtering with RAS policies:
1. Create a Policy using instructions from Parallels RAS Administrator's Guide.
2. Switch to Apply the policy to and click [+].
3. New rule configuration window opens.
4. Add different criteria and adjust values based on requirements.
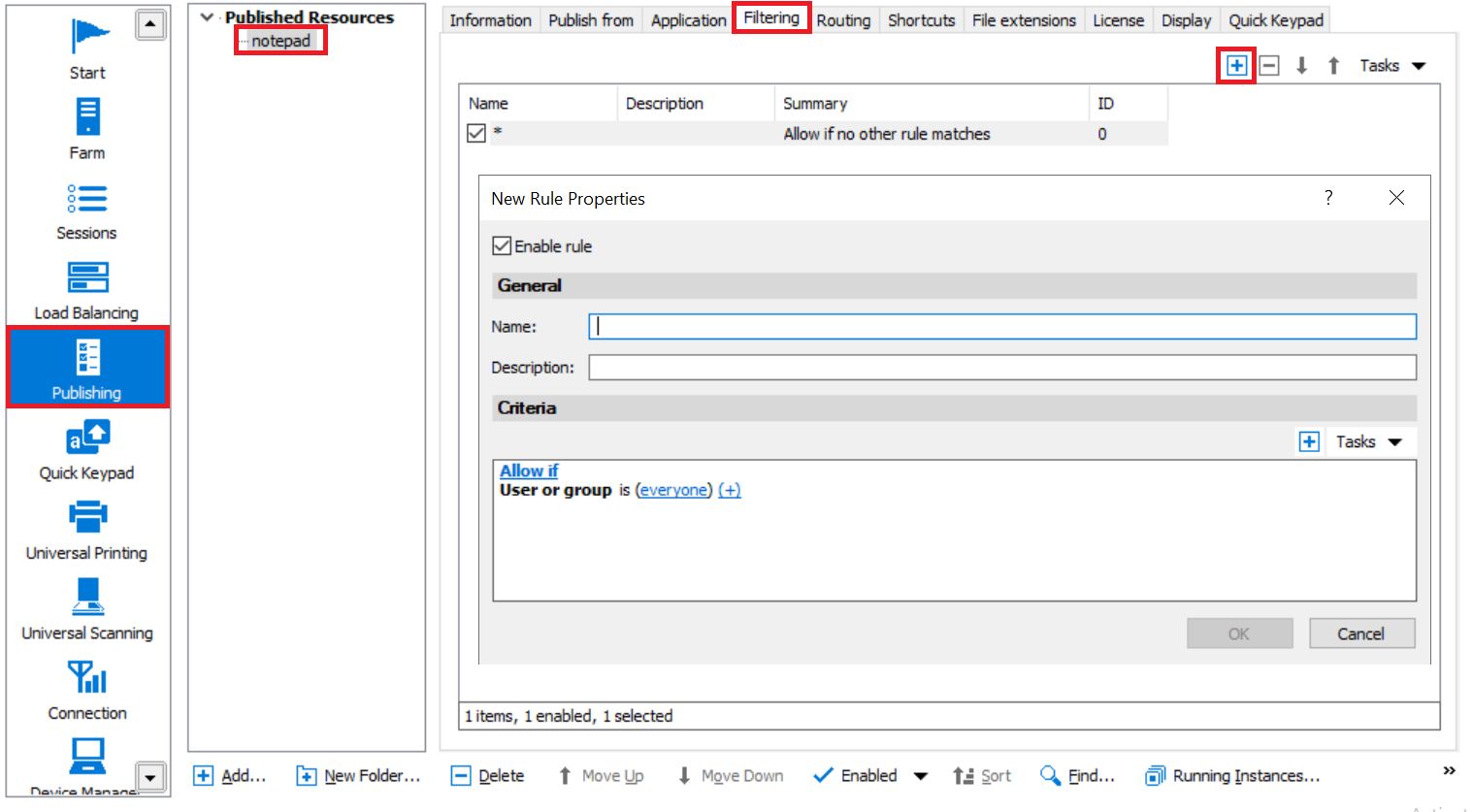
Using expression-based filtering with Published Items:
1. Publish any item using instructions from Parallels RAS Administrator's Guide.
2. Switch to the Filtering tab and click [+].
3. New rule configuration window opens.
4. Add different criteria and adjust with values based on requirements.
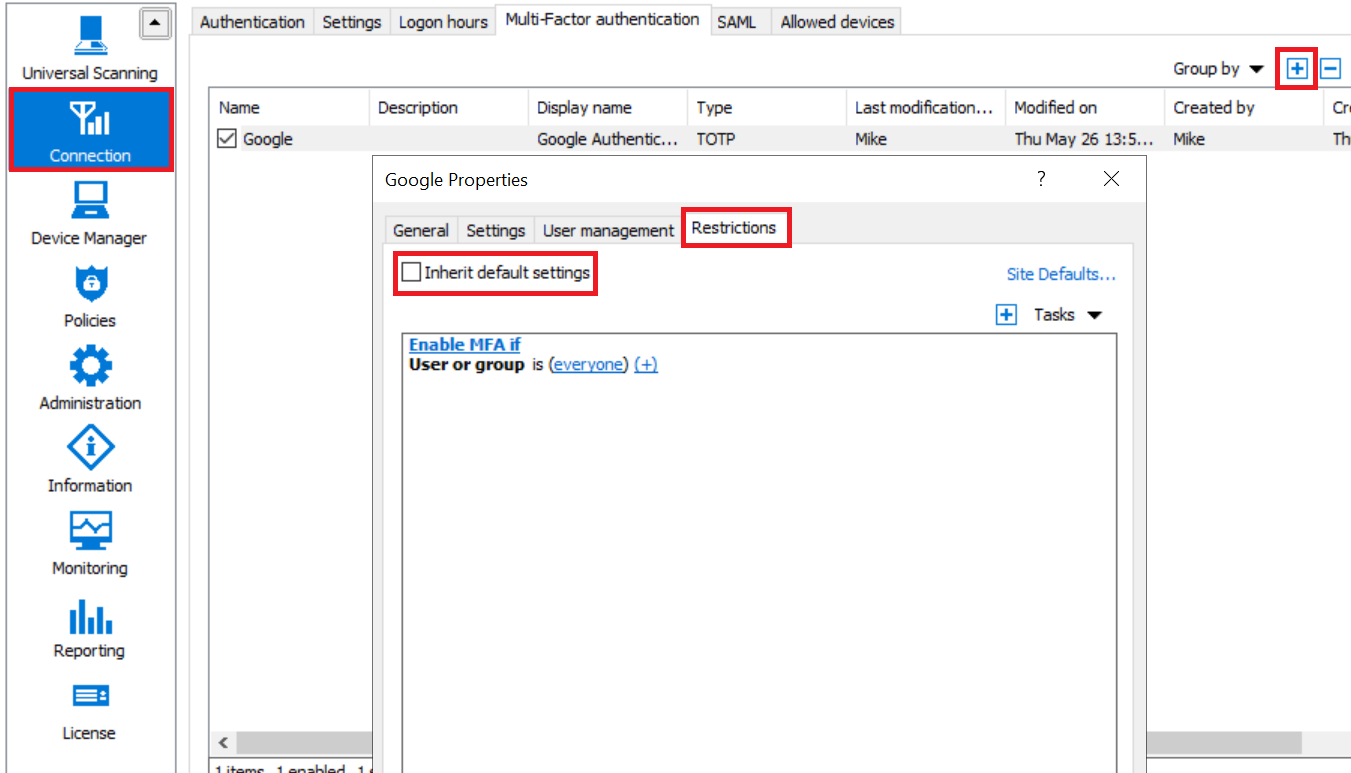
Using expression-based filtering with MFA restrictions:
1. Enable and configure the MFA solution using instructions from Parallels RAS Administrator's Guide and instructions from the solution vendor where applicable.
2. Open MFA properties and switch to the Restrictions tab.
3. Uncheck Inherit default settings flag.
4. Adjust criteria to either request MFA for a user or allow the user to pass it over.
Known Issues and Limitations
By design, a rule cannot have two criteria of the same type. For example, you cannot allow access to a published resource to one group of users and deny access to the same resource to another group of users in the same rule. To do this, you will need to create two rules.
Was this article helpful?
Tell us how we can improve it.