This article describes how to set up DUO MFA in Parallels RAS.
1. Download Duo Proxy Authenticator. Use the default installation instructions, and you will notice that Duo service is not running in services.msc. This is expected because authproxy.conf has to be configured for your environment.
2. Open Windows Explorer, navigate to C:\Program Files (x86)\Duo Security Authentication Proxy\conf and open authproxy.cfg:
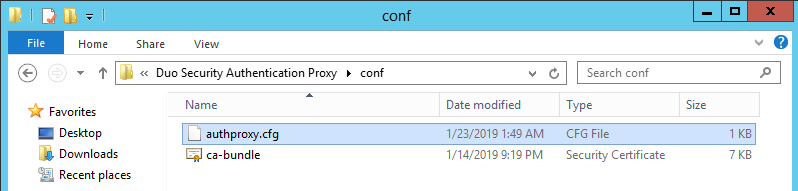
3. The configuration file has several unnecessary settings, and for typical RAS integration, we should configure the following:
[ad_client] is to use an Active Directory domain controller to perform primary authentication. This section accepts the following options:
service_account_username - The username of an account that has permission to read from your Active Directory database;
service_account_password - The password corresponding to service_account_username;
search_dn - The LDAP distinguished name (DN) of an Active Directory container or organizational unit (OU) containing all of the users you wish to permit to log in;
security_group_dn - To further restrict access, specify the LDAP distinguished name (DN) of a security group that contains the users who should be able to log in. Others users will not pass primary authentication.
[duo_only_client] - to use Authentication Proxy for secondary authentication and let the Publishing Agent handle primary authentication independently. This section has no additional properties to configure.
[radius_server_duo_only] - to use a RADIUS integration that does not handle primary authentication credentials. The user's passcode or factor choice, encrypted using the PAP mechanism, is submitted for the RADIUS password.
ikey - Your Duo integration key;
skey - Your Duo secret key;
api_host - Your Duo API hostname (e.g., “api-XXXXXXXX.duosecurity.com”);
radius_ip_1 - IP address of your RAS Publishing Agent.
radius_secret_1 - The secret key that you will specify in step 6;
radius_ip_2 - IP address of your secondary Publishing Agent if you have any. If you have only one PA, don't add this line;
radius_secret_2 - The same secret key as for radius_secret_1. If you have only one PA, don't add this line;
failmode - Either "safe" or "secure" defines the behavior of the system when Duo's service cannot be contacted. When set to "safe," authentication attempts will be permitted if primary authentication succeeds. When set to "secure," all users' authentication attempts will be rejected.
client - The mechanism that the Authentication Proxy should use to perform primary authentication. This should correspond with a "client" section elsewhere in the config file. Set this value either to ad_client to use Active Directory for primary authentication OR to duo_only_client to utilize Authentication Proxy for secondary authentication only.
[ad_client] section configured.
port - Port on which to listen for incoming RADIUS Access Requests. By default, the proxy will listen on port 1812.
Example for "ad_client":
Example for "duo_only_client":
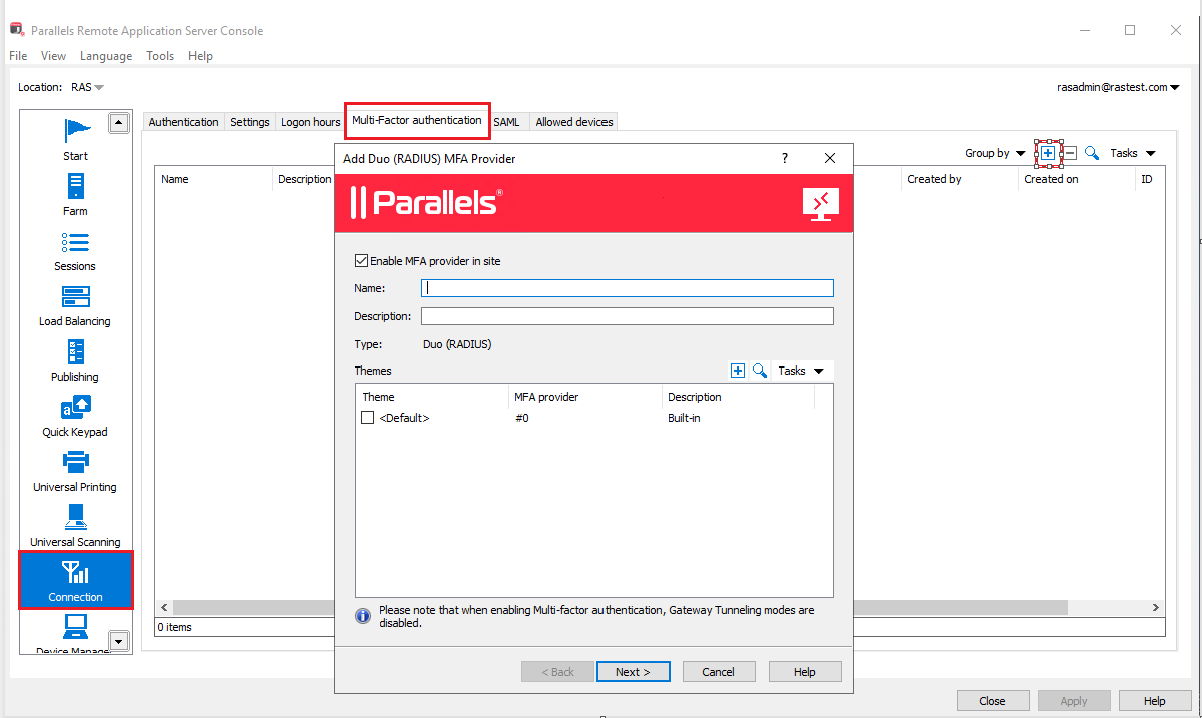
5. Configure RAS to communicate with Duo: RAS Console → Farm → Connections → Multi-Factor authentication Tab. Click on the "+" symbol and choose Radius and select DUO.
6. Configure connection settings:
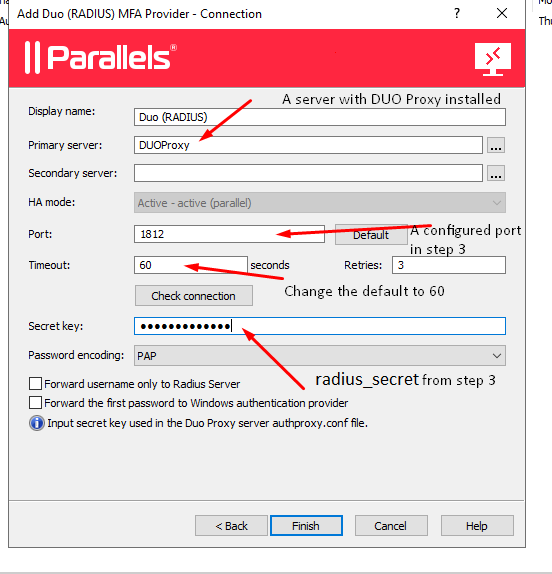
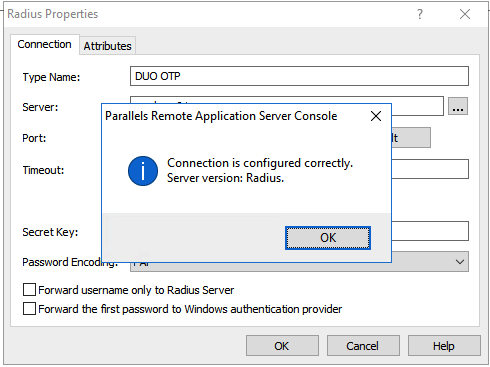
7. Click on Check Connection, and you should see the Success result:
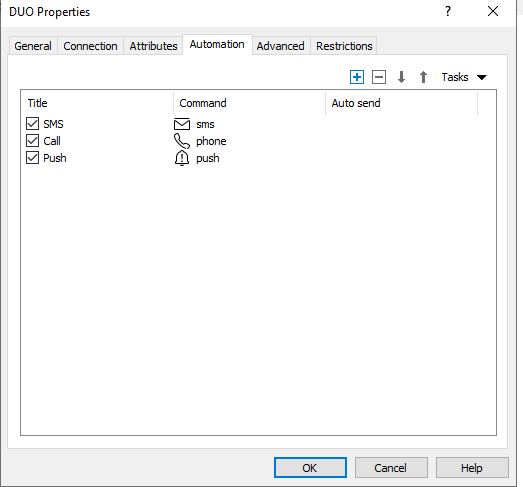
8. Optionally, you may configure additional 2FA method: phone call, SMS. Use the Automation tab and create the desired way.
9. Click Apply, and the next time users log on, they will have 2-factor-authentication enabled.

Was this article helpful?
Tell us how we can improve it.