Symptoms
Authentication issues when using single sign-on (SSO).
Cause
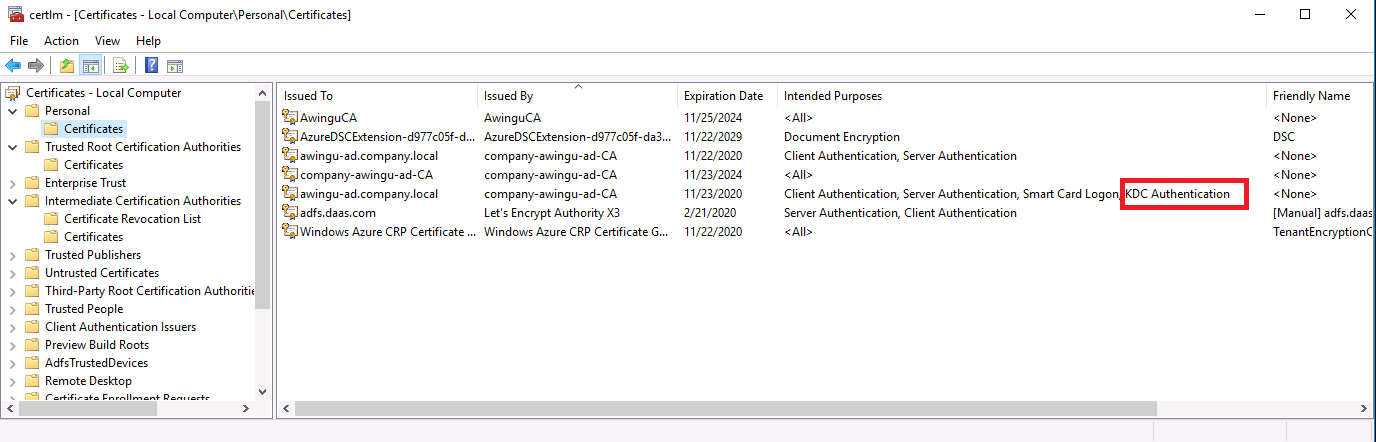
The Kerberos Domain Controller has no valid certificate for the intended purposes (Client Authentication, Server Authentication, KDC Authentication and Smartcard Logon).
Resolution
- On each Microsoft Windows Kerberos Domain Controller, press [Win] + R.
- Enter certlm.msc and press [OK] to launch the management console showing the certificates of the local computer.
- Navigate to Personal > Certificates.
- Check that you have a valid KDC Authentication Certificate for each Domain Controller.
- It should be present.
- It should NOT be expired, it should still be valid.
- In the "Intended purposes" column:
- It should explicitly list these 4 purposes (the order does not matter):
- Server Authentication
- Client Authentication
- Smartcard Logon
- KDC Authentication
- The purpose should NOT be set to <All>. Surprisingly, this can lead to errors on the Microsoft Windows Server side.
- It should explicitly list these 4 purposes (the order does not matter):
Note: if there were other certificates being used by the KDCs, it may be necessary to restart the "Kerberos Key Distribution Center" service on the Microsoft Windows Server to make sure the Kerberos service uses the new certificate.
Was this article helpful?
Tell us how we can improve it.